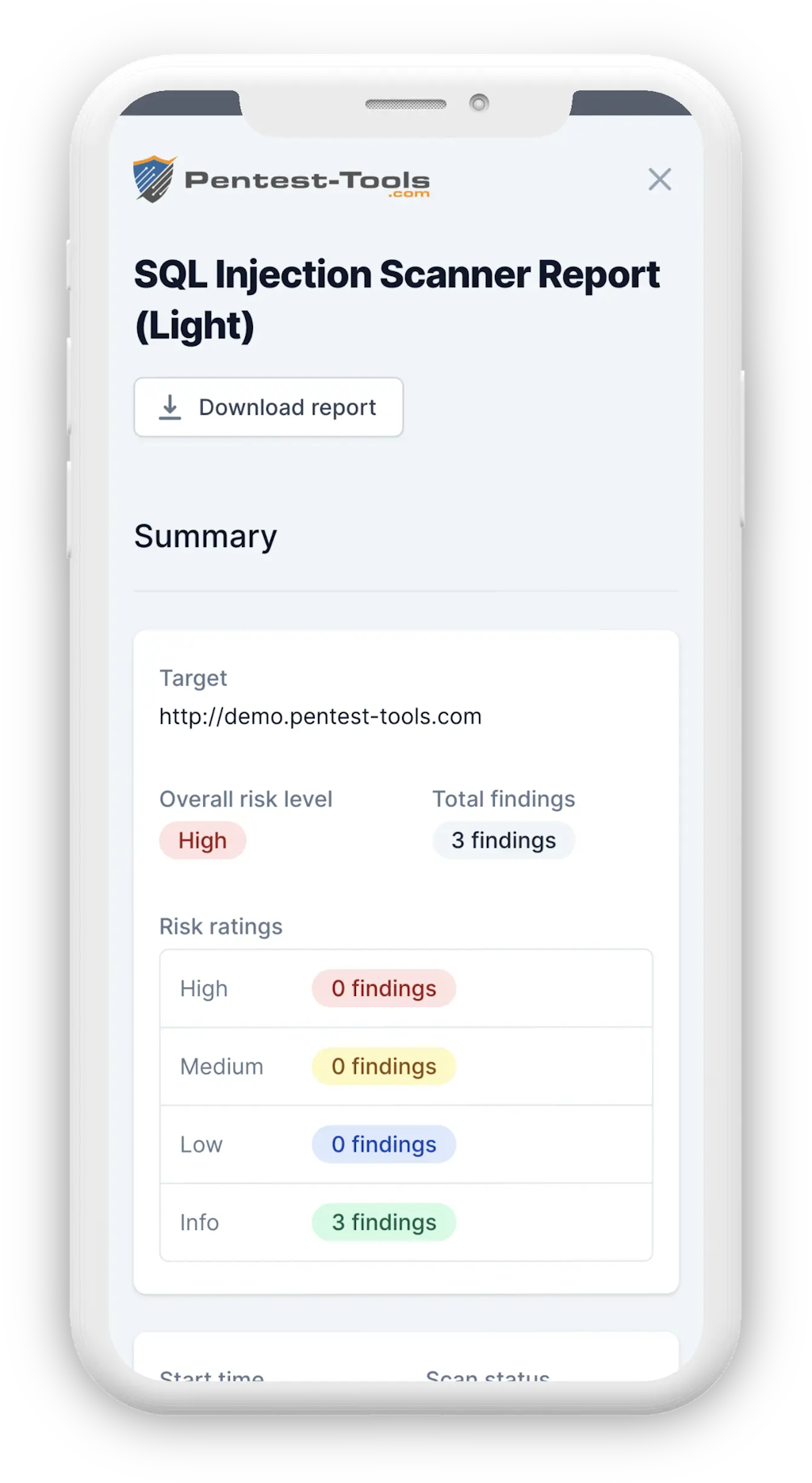
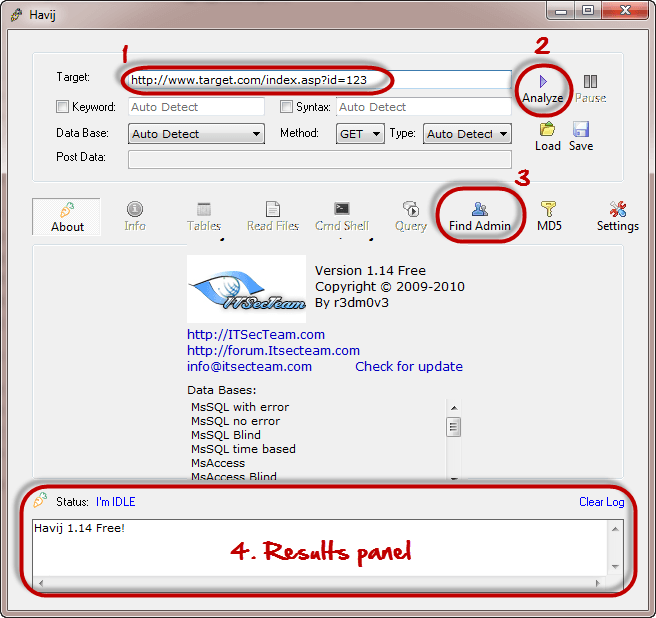
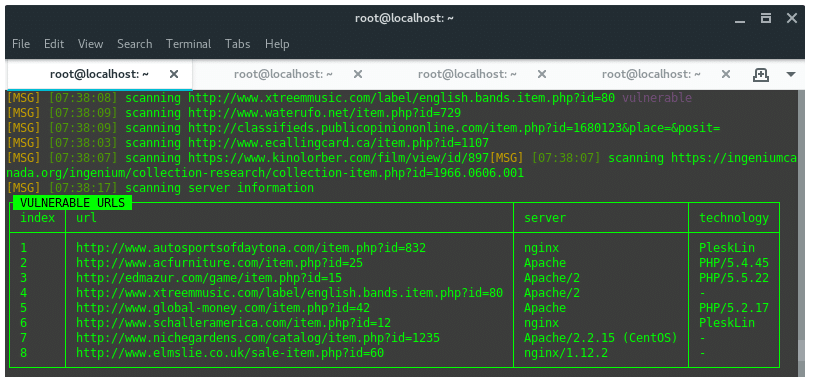
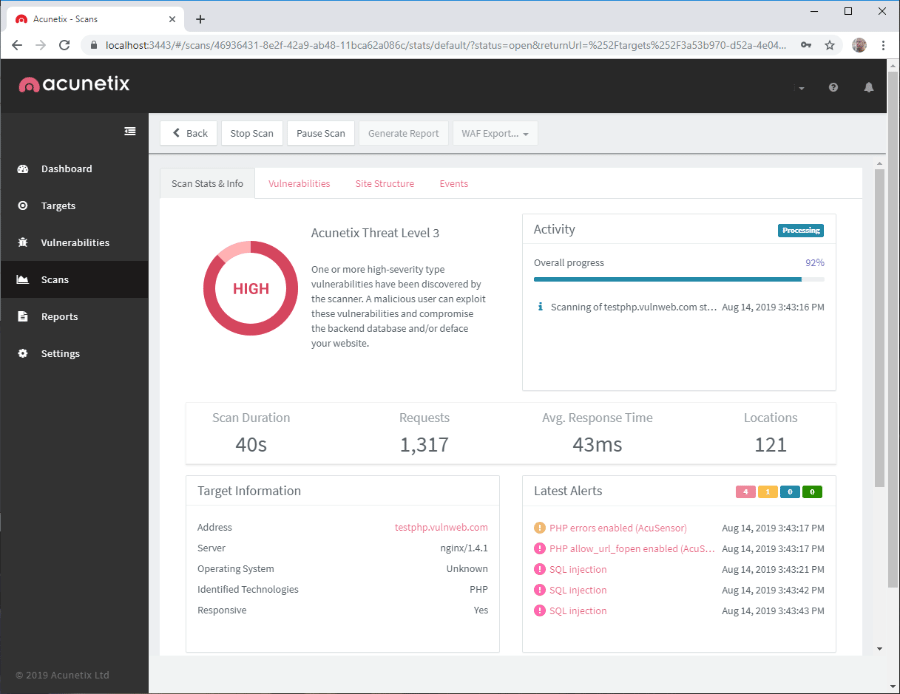
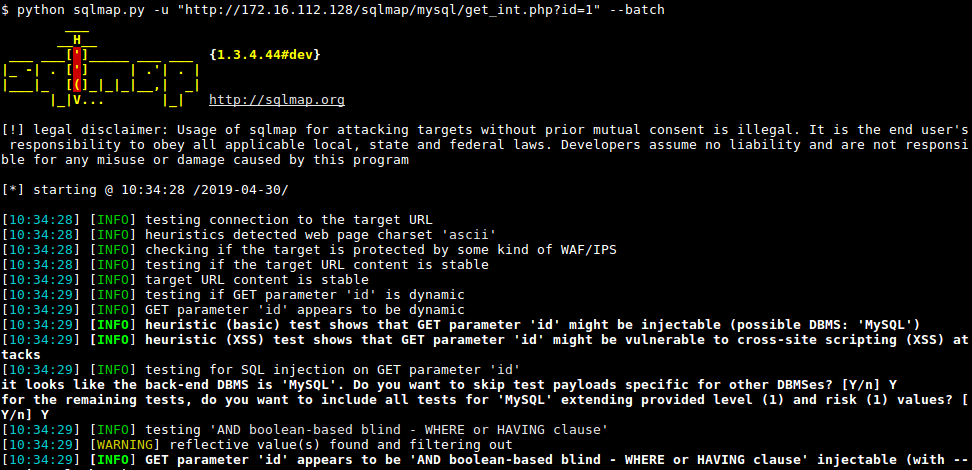
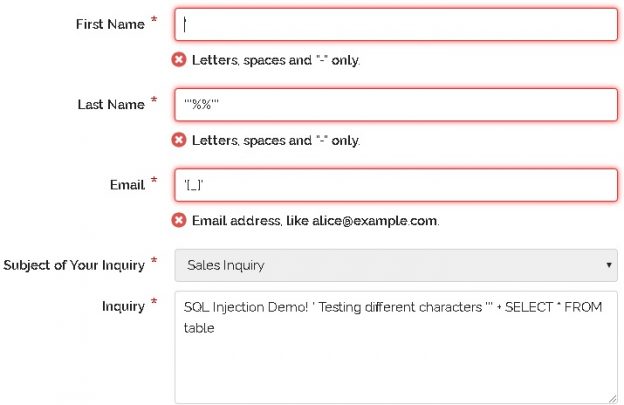
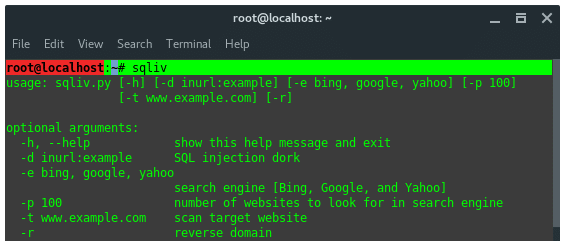
jSQL Injection usage guide: a multifunctional tool for scanning and exploiting SQL injection in Kali Linux - Ethical hacking and penetration testing

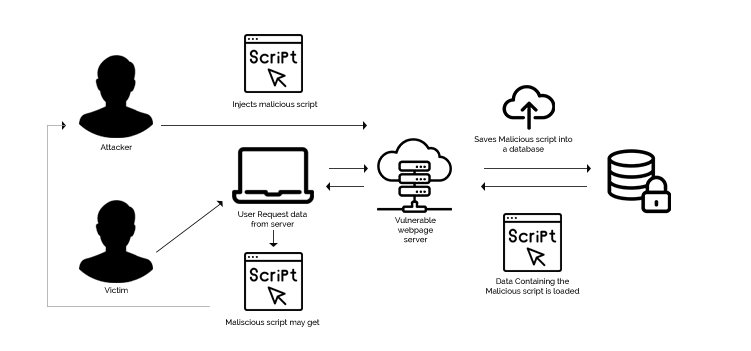
R-WASP Framework for detection and prevention of SQL injection from... | Download Scientific Diagram